Chinese Hackers Use CloudScout Toolset to Steal Session Cookies from Cloud Services
- November 4, 2024
- Posted by: claudia
- Categories:
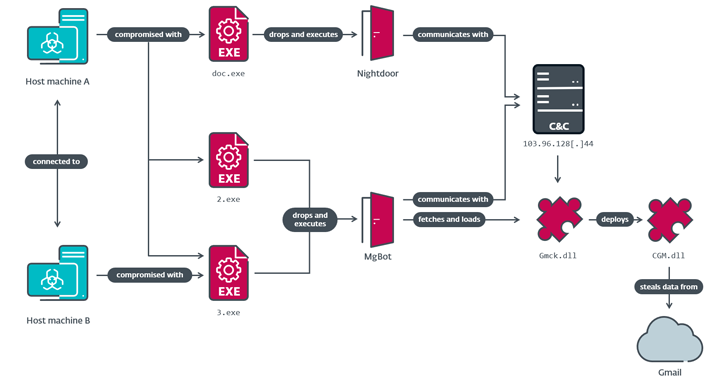
Evasive Panda, a China-linked cyber espionage group, has recently targeted a government entity and a religious organization in Taiwan using a newly discovered malware toolset known as CloudScout. This post-compromise toolset allows attackers to harvest information from various cloud services by exploiting stolen web session cookies. Security researcher Anh Ho from ESET confirmed that CloudScout operates as an extension to Evasive Panda’s main malware framework, MgBot, facilitating unauthorized access to critical online storage and communication platforms.
CloudScout’s detection occurred between May 2022 and February 2023, revealing a sophisticated array of tools. The malware is comprised of ten different modules, primarily coded in C#, with three specifically designed to extract data from Google Drive, Gmail, and Outlook. The functionalities of the remaining modules have yet to be uncovered. Evasive Panda, also known by various aliases including Bronze Highland, Daggerfly, and StormBamboo, has established a pattern of targeting a range of organizations in Taiwan and Hong Kong, demonstrating a penchant for complex cyber attacks such as watering hole and supply chain compromises.
The group employs a variety of initial access vectors, utilizing disclosed security vulnerabilities and methods like DNS poisoning to establish footholds in victim networks. Once inside, Evasive Panda can deploy both MgBot and Nightdoor malware. The CloudScout modules function by hijacking browser sessions through a method known as “pass-the-cookie,” enabling the extraction of private information and email content.
Central to this toolset is the CommonUtilities package, which provides essential low-level libraries required for the modules’ operations. This package includes custom libraries such as HTTPAccess, ManagedCookie, Logger, and SimpleJSON, which enhance the control developers have over the tool’s functionality, surpassing what is available through standard open-source libraries.
The malware’s capabilities allow it to gather sensitive data such as email folder listings, messages (including attachments), and specific file types, which are then compressed into ZIP archives for exfiltration via MgBot or Nightdoor. ESET analysts warn that emerging security measures, including Device Bound Session Credentials and App-Bound Encryption from Google, are poised to nullify the efficacy of cookie-theft malware like CloudScout in the future.
This alarming trend coincides with mounting concerns from other jurisdictions, particularly as the Government of Canada has reported extensive reconnaissance activities perpetrated by a sophisticated Chinese state-sponsored threat actor. Their efforts span a wide array of targets, including governmental agencies, political parties, and critical infrastructure organizations, highlighting the growing sophistication and reach of such cyber threats.
Consequently, these developments underscore an urgent need for heightened cybersecurity awareness and measures among organizations at risk, especially those in politically sensitive or high-stakes environments. As cyber espionage tactics evolve, staying ahead of such threats is crucial to safeguard sensitive data and maintain operational integrity across various sectors.
The rise of sophisticated threat actors like Evasive Panda confirms the ongoing and escalating challenges in the cybersecurity landscape, prompting a reevaluation of protective strategies and collaborative responses among nations and organizations affected by these aggressive cyber campaigns.
