CosmicBeetle steps up: Probation period at RansomHub
- November 4, 2024
- Posted by: claudia
- Categories:
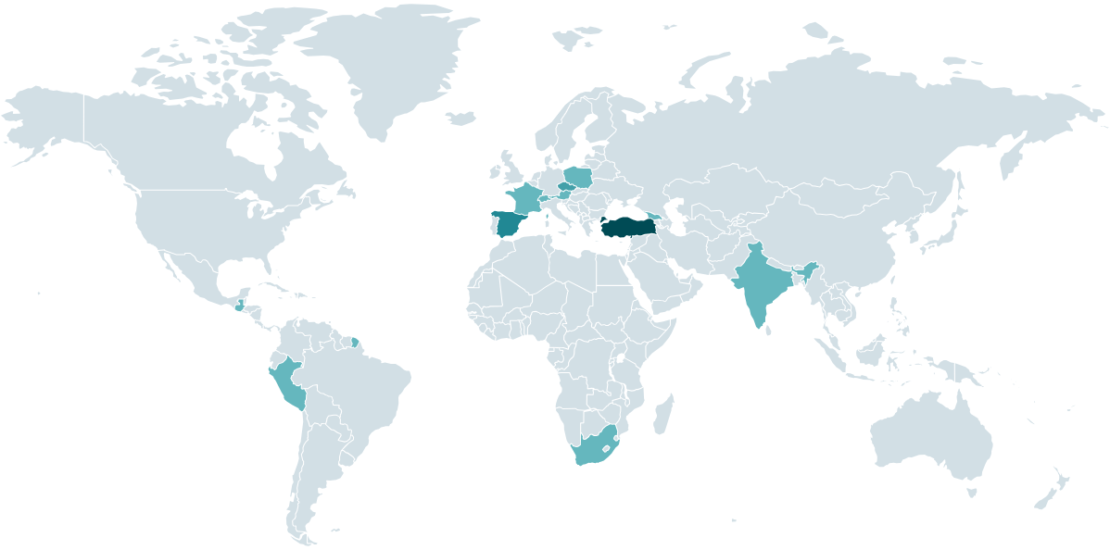
ESET researchers have recently explored the operations of the CosmicBeetle threat actor, revealing its deployment of a new ransomware variant named ScRansom. This group, which has been active since at least 2020, emerged prominently in 2023 with notable activities against small and medium-sized businesses (SMBs) worldwide. CosmicBeetle has transitioned from utilizing the Scarab ransomware to its custom-developed ScRansom, which, despite its ongoing improvements, demonstrates a lack of sophistication typical of immature ransomware actors.
CosmicBeetle has shown a strategic inclination towards leveraging established ransomware brands, notably attempting to exploit the reputation of LockBit, a well-known ransomware gang. The group has been observed using a leaked LockBit builder to craft its ransomware samples while incorporating elements of LockBit’s presentation in ransom communications, aiming to increase the likelihood of victim compliance through fear and perceived legitimacy. Additionally, there are indications that CosmicBeetle may be a new affiliate of RansomHub, a new ransomware-as-a-service entity, which began operations in March 2024 and has quickly gained attention due to its rising activity.
The analysis delves deeply into CosmicBeetle’s methodology, showcasing its techniques for exploiting long-standing vulnerabilities in software commonly used by SMBs. The telemetry data indicates that targets across various sectors, including manufacturing, healthcare, legal, and technology, have been victimized. As CosmicBeetle’s operations expand in 2024, its ScRansom toolset continues to evolve and develop, leading to potential complications for encryption and decryption processes.
ScRansom itself has been characterized as a relatively unrefined ransomware variant that struggles with deployment issues, which has resulted in some cases where victims who pay the ransom still cannot recover all their data. Although the decryption process aligns with traditional methods—requiring victims to request a protection key from the threat actor—it is fraught with complications. Multiple files may need distinct keys, and in certain cases, the chosen encryption modes lead to permanent data loss.
CosmicBeetle employs various targeting strategies, including brute-force attacks and exploitation of known vulnerabilities, to gain initial access to its targets. Notably, their cyberattack strategies rely on user execution following interactive deployment, which separates their operations from more automated, refined ransomware deployments. Their evolving tactics include the potential use of remote desktop protocol (RDP) access to manipulate victim systems directly.
As the group continues to hone its technical capabilities, cosmic activity has been recorded regarding ScRansom’s encryption technique. The ransomware employs a somewhat convoluted encryption scheme utilizing multiple layers of symmetric and asymmetric encryption, presenting significant difficulties for victim recovery efforts. These complexities likely stem from the group’s relative inexperience in the ransomware arena, resulting in a complicated decryption process that may frustrate victims trying to regain access to their files.
ESET’s telemetry tracking of CosmicBeetle’s operations throughout 2023 and into 2024 unveils a distinct pattern of ransomware deployment that relies heavily on both brute-force methods and the adoption of tools from more notorious ransomware organizations. The tracking data also revealed instances of overlap with RansomHub’s malicious activities, solidifying suspicions regarding CosmicBeetle’s potential affiliations.
Investigations into the branding decisions made by CosmicBeetle indicate confusion and inconsistency, particularly in ransomware naming conventions—at times, they simply referred to their operations as “NONAME.” This branding approach mimics the notorious LockBit in design and execution, aimed likely to foster a false sense of security among victims.
Furthermore, the unauthorized use of LockBit’s digital infrastructure—including the creation of lookalike leak sites—further illustrates the lengths to which CosmicBeetle is willing to go to leverage established ransomware reputations to its advantage. This includes manipulation through various communication channels and platforms, as highlighted by their use of encrypted messaging for ransom negotiations.
In conclusion, the ongoing analysis of CosmicBeetle’s development and deployment of ScRansom emphasizes the challenges posed by emerging ransomware actors that seek to integrate and emulate established strategies from successful criminal enterprises. As ransomware technology becomes increasingly complex, the potential for inconsistent and ineffective methodologies may result in significant challenges for both victims during recovery and for researchers tracking their activities. As such, ESET researchers continue to monitor developments in the ever-evolving ransomware landscape to provide vital insights into the actions of threat actors like CosmicBeetle.
