New Android Banking Malware ‘ToxicPanda’ Targets Users with Fraudulent Money Transfers
- November 5, 2024
- Posted by: claudia
- Categories:
A new strain of Android banking malware, named ToxicPanda, has infected over 1,500 devices, primarily targeting retail banking users in Europe and Latin America. Researchers from Cleafy identified that the malware aims to facilitate fraudulent banking transactions through account takeover by employing a technique known as on-device fraud (ODF). By circumventing traditional identity verification and behavioral detection used by banks, ToxicPanda represents a significant threat.
The malware demonstrates similarities to an earlier Android malware, TgToxic, which was known for stealing credentials and funds from cryptocurrency wallets. The majority of ToxicPanda compromises have been reported in Italy (56.8%), along with notable infections in Portugal, Hong Kong, Spain, and Peru. Its emergence indicates a rare operation from a Chinese-speaking threat actor focusing on fraudulent activities against consumers in these regions.
ToxicPanda is still in its infancy, displaying a simpler version than its predecessor by stripping down features such as Automatic Transfer System (ATS) and Easyclick, while introducing 33 new commands for data harvesting. Although 61 commands are shared with TgToxic, substantial divergences indicate either a new lineage or modifications under the same operational umbrella, as many functions typical to TgToxic are notably absent.
The malware often disguises itself as legitimate applications, like Google Chrome and Visa, using counterfeit app store listings for distribution. The method by which these malicious links proliferate remains unclear, but could potentially involve malvertising or smishing tactics. Upon installation via sideloading, ToxicPanda utilizes Android’s accessibility services for elevated permissions, enabling it to capture inputs and data from various applications.
Another significant threat posed by ToxicPanda is its ability to intercept one-time passwords (OTPs) sent via SMS or generated by authenticator applications. This capability allows attackers to bypass two-factor authentication (2FA), facilitating unauthorized transactions undetected by victims. The malware grants remote control of infected devices, enabling attackers to execute ODF for fraudulent financial activities.
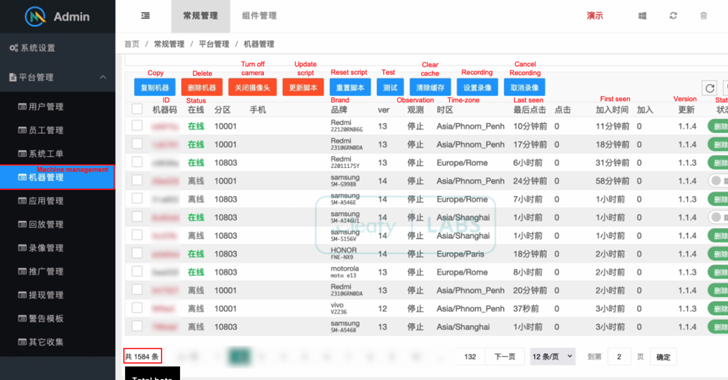
Researchers at Cleafy managed to access the command-and-control (C2) panel of ToxicPanda, which is displayed in Chinese. This interface provides insight into the list of compromised devices, including their model and location, and allows operators to request real-time control over devices for executing ODF maneuvers.
Though some functions of ToxicPanda are minimal, the presence of artifacts indicative of early developmental stages—such as logging, dead code, and debugging files—suggests that it could be undergoing significant refactoring efforts or is not yet fully realized in terms of its potential capabilities.
In response to malign activities exploiting Android’s accessibility features, researchers from the Georgia Institute of Technology and other institutions have introduced a backend service titled DVa (Detector of Victim-specific Accessibility). This tool leverages dynamic execution traces and an advanced analytical strategy for detecting and categorizing abuse routines, thus contributing to understanding how malware can obfuscate legal inquiries or uninstall attempts.
As ToxicPanda represents an evolving threat landscape, its development warrants close monitoring, particularly as new techniques in the malware are deployed against increasingly vigilant banking security measures. The emergence of tools like DVa signals a proactive stance in combating such vulnerabilities in mobile security.
