-
German Police Disrupt DDoS-for-Hire Platform dstat[.]cc; Suspects Arrested
- November 4, 2024
- Posted by: claudia
- Categories:
No Comments![German Police Disrupt DDoS-for-Hire Platform dstat[.]cc; Suspects Arrested](https://boztek.com/wp-content/uploads/2024/11/German-Police-Disrupt-DDoS-for-Hire-Platform-dstatcc-Suspects-Arrested.png)
German law enforcement has disrupted dstat[.]cc, a criminal platform enabling individuals to easily conduct DDoS attacks. This service, accessible even to those lacking technical skills, provided reviews of stresser services, aiding in the execution of attacks against targeted websites.
-
SEC Charges 4 Companies Over Misleading SolarWinds Cyber Attack Disclosures
- November 4, 2024
- Posted by: claudia
- Categories:

The SEC has charged four companies—Avaya, Check Point, Mimecast, and Unisys—for misleading disclosures related to the SolarWinds cyberattack in 2020. The companies downplayed the extent of the breach, resulting in penalties totaling $6 million and violations of federal securities laws.
-
Is Your Identity Security AI-Proof?
- November 4, 2024
- Posted by: claudia
- Categories:
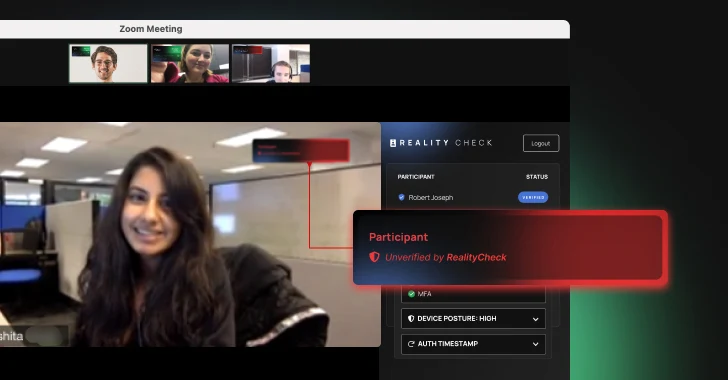
AI has transformed from a mere concept to a significant threat, with AI impersonation fraud on the rise. Current detection methods struggle to keep pace with attackers. A secure-by-design identity platform, like Beyond Identity’s RealityCheck, offers robust defenses against this emerging danger.
-
Apple Opens PCC Source Code for Researchers to Identify Bugs in Cloud AI Security
- November 4, 2024
- Posted by: claudia
- Categories:

Apple has launched its Private Cloud Compute (PCC) Virtual Research Environment (VRE) for scrutiny by the research community, promoting transparency and security in its cloud AI services. The iPhone maker invites researchers to verify its privacy claims and offers substantial rewards for identified vulnerabilities.
-
Researchers Discover Command Injection Flaw in Wi-Fi Alliance’s Test Suite
- November 4, 2024
- Posted by: claudia
- Categories:

A security flaw in the Wi-Fi Test Suite can allow unauthenticated local attackers to execute arbitrary code on Arcadyan FMIMG51AX000J routers. Tracked as CVE-2024-41992, this vulnerability enables attackers to gain full administrative control, risking network integrity.
-
CERT-UA Identifies Malicious RDP Files in Latest Attack on Ukrainian Entities
- November 4, 2024
- Posted by: claudia
- Categories:
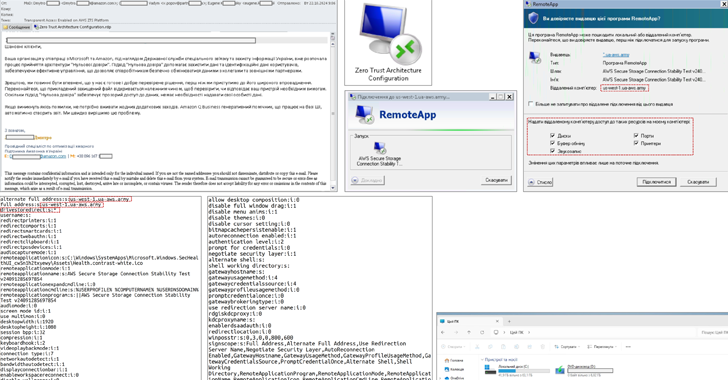
CERT-UA has reported a dangerous email campaign targeting Ukrainian governmental and military entities. The attackers utilize deceptive emails featuring Remote Desktop Protocol (RDP) files. Once executed, these files allow threat actors to gain remote access, steal data, and spread malware.
-
Four REvil Ransomware Members Sentenced in Rare Russian Cybercrime Convictions
- November 4, 2024
- Posted by: claudia
- Categories:

Four members of the defunct REvil ransomware group have been sentenced to prison in Russia for hacking and money laundering. The court found them guilty of illegal payment circulation and malware distribution, with sentences ranging from 4.5 to 6 years.
-
Notorious Hacker Group TeamTNT Launches New Cloud Attacks for Crypto Mining
- November 4, 2024
- Posted by: claudia
- Categories:
The notorious cryptojacking group TeamTNT is gearing up for a large-scale campaign targeting cloud-native environments to mine cryptocurrencies. They aim to deploy Sliver malware via exposed Docker daemons while renting out compromised servers to others for illicit mining activities.
-
Researchers Uncover OS Downgrade Vulnerability Targeting Microsoft Windows Kernel
- November 4, 2024
- Posted by: claudia
- Categories:
A new attack technique has emerged that bypasses Microsoft’s Driver Signature Enforcement on fully patched Windows systems, enabling OS downgrade attacks. This vulnerability allows the loading of unsigned kernel drivers, which can lead to malicious rootkit deployment, compromising system security.
-
Sailing the Seven Seas Securely from Port to Port – OT Access Security for Ships and Cranes
- November 4, 2024
- Posted by: claudia
- Categories:

Operational Technology (OT) security is increasingly vital as marine vessel and port operators digitize and automate systems. This shift introduces new security challenges, emphasizing the need for secure remote access management for industrial control systems (ICS). Learn more in our guide.
Contact us at the Consulting WP office nearest to you or submit a business inquiry online.
