-
Google’s AI Tool Big Sleep Finds Zero-Day Vulnerability in SQLite Database Engine
- November 4, 2024
- Posted by: claudia
- Categories:
No Comments
Google’s Big Sleep framework has uncovered a zero-day vulnerability in the SQLite database engine, marking a significant milestone in AI-assisted security. The exploit involves a stack buffer underflow, which can cause crashes or arbitrary code execution.
-
Cyber Threats That Could Impact the Retail Industry This Holiday Season (and What to Do About It)
- November 4, 2024
- Posted by: claudia
- Categories:

As the holiday season nears, retailers brace for increased traffic, but this surge attracts cybercriminals exploiting vulnerabilities. Imperva’s cybersecurity guide highlights that AI-driven threats pose significant risks, with daily attacks averaging 569,884 on retail sites.
-
Cybercriminals Use Webflow to Deceive Users into Sharing Sensitive Login Credentials
- November 4, 2024
- Posted by: claudia
- Categories:
Cybersecurity researchers have reported a surge in phishing attacks utilizing Webflow, targeting sensitive crypto wallet information. The campaigns have increased tenfold from April to September 2024, affecting over 120 organizations mainly in North America and Asia.
-
BeaverTail Malware Resurfaces in Malicious npm Packages Targeting Developers
- November 4, 2024
- Posted by: claudia
- Categories:

Three malicious npm packages identified in September 2024 contain BeaverTail malware, linked to a North Korean campaign named Contagious Interview. Datadog’s research highlights the ongoing exploitation of the open-source software supply chain for malware distribution.
-
Russian Espionage Group Targets Ukrainian Military with Malware via Telegram
- November 4, 2024
- Posted by: claudia
- Categories:

A suspected Russian espionage group, UNC5812, is delivering Windows and Android malware to target the Ukrainian military via a Telegram channel named Civil Defense. The malware uses deceptive applications to install spyware, while undermining military recruitment efforts.
-
THN Cybersecurity Recap: Top Threats, Tools and News (Oct 21
- November 4, 2024
- Posted by: claudia
- Categories:

This week in cybersecurity unveils critical exploits, including a serious Fortinet flaw allowing remote code execution and an AI tool vulnerability. Discover the latest threats, from cryptographic issues in cloud storage to the activities of the notorious Lazarus Group. Stay informed!
-
Chinese Hackers Use CloudScout Toolset to Steal Session Cookies from Cloud Services
- November 4, 2024
- Posted by: claudia
- Categories:
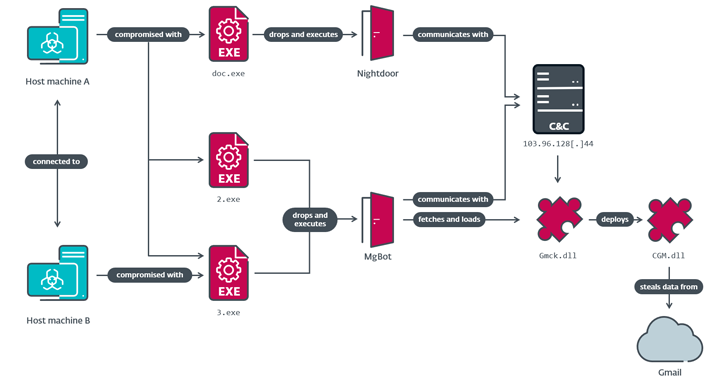
Evasive Panda, a China-linked cyber espionage group, targeted a Taiwanese government entity and a religious organization with a new toolset, CloudScout. This .NET-based malware steals data from cloud services using stolen session cookies through its integrations with MgBot.
-
New Research Reveals Spectre Vulnerability Persists in Latest AMD and Intel Processors
- November 4, 2024
- Posted by: claudia
- Categories:

New research reveals that AMD and Intel processors remain vulnerable to speculative execution attacks, even six years after the Spectre flaw was identified. ETH Zürich’s study shows a microcode bug could allow bypassing Indirect Branch Predictor Barrier, exposing sensitive data.
-
U.S. Government Issues New TLP Guidance for Cross-Sector Threat Intelligence Sharing
- November 4, 2024
- Posted by: claudia
- Categories:

The U.S. government has released new guidance on the Traffic Light Protocol (TLP) for sharing threat intelligence among the private sector, researchers, and federal agencies. This framework promotes trust and secure collaboration in cybersecurity by classifying sensitive information into color-coded categories.
-
Dutch Police Disrupt Major Info Stealers RedLine and MetaStealer in Operation Magnus
- November 4, 2024
- Posted by: claudia
- Categories:

International law enforcement, led by the Dutch National Police, disrupted the infrastructure behind malware RedLine and MetaStealer. This operation, part of Operation Magnus, resulted in the shutdown of servers, arrest of individuals, and a significant blow to cybercrime operations.
Contact us at the Consulting WP office nearest to you or submit a business inquiry online.
