-
Embarking on a Compliance Journey? Here’s How Intruder Can Help
- November 4, 2024
- Posted by: claudia
- Categories:
No Comments
Navigating compliance frameworks like ISO 27001 and GDPR can be challenging. Intruder simplifies this process by addressing key vulnerability management criteria, helping you maintain security. With continuous scanning and automated reporting, stay ahead of threats effortlessly.
-
Researchers Uncover Python Package Targeting Crypto Wallets with Malicious Code
- November 4, 2024
- Posted by: claudia
- Categories:

Researchers uncovered a malicious Python package disguised as a cryptocurrency trading tool, named “CryptoAITools.” Installed on Windows and macOS, it automates data theft from crypto wallets and sensitive info, enabling attackers to drain victims’ assets.
-
Malvertising Campaign Hijacks Facebook Accounts to Spread SYS01stealer Malware
- November 4, 2024
- Posted by: claudia
- Categories:
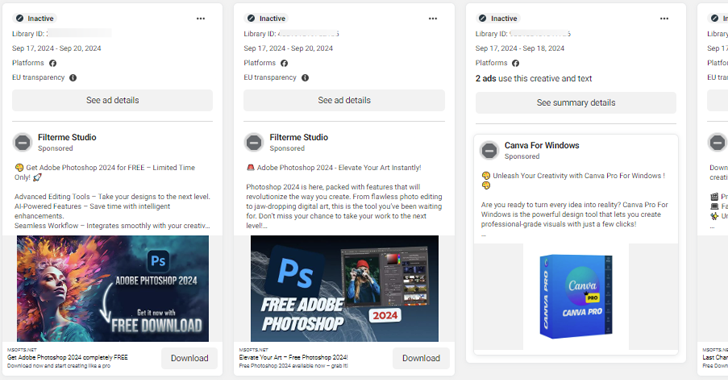
Cybersecurity researchers have uncovered a malvertising campaign exploiting Meta’s ad platform to distribute SYS01stealer malware. This operation uses hijacked Facebook accounts and trusted brands, targeting users with deceptive ads that lead to credential theft and further malvertising.
-
Opera Browser Fixes Big Security Hole That Could Have Exposed Your Information
- November 4, 2024
- Posted by: claudia
- Categories:
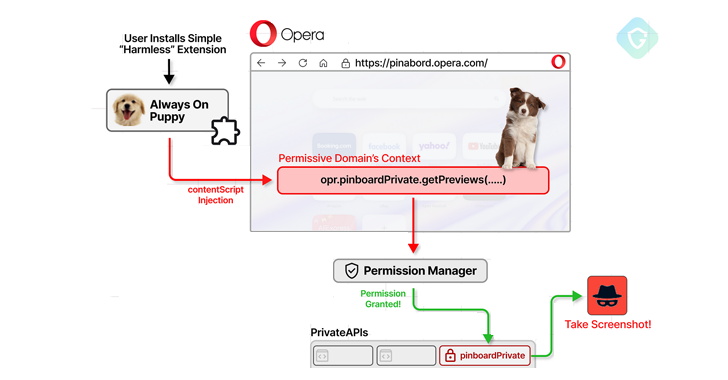
A recently patched security flaw in the Opera web browser, named “CrossBarking,” could have allowed a malicious extension to access private APIs, enabling actions like taking screenshots and hijacking accounts. This incident underscores the risks of browser extensions.
-
North Korean Group Collaborates with Play Ransomware in Significant Cyber Attack
- November 4, 2024
- Posted by: claudia
- Categories:

Threat actors linked to North Korea’s Jumpy Pisces group have collaborated with the Play ransomware operation, marking a significant development. Observed between May and September 2024, this collaboration indicates a shift where state-sponsored groups could leverage underground ransomware networks for financial gain.
-
LiteSpeed Cache Plugin Vulnerability Poses Significant Risk to WordPress Websites
- November 4, 2024
- Posted by: claudia
- Categories:

A high-severity vulnerability in the LiteSpeed Cache plugin for WordPress (CVE-2024-50550) allows unauthenticated users to gain admin-level access, posing a significant security risk. This flaw has been addressed in version 6.5.2 and stems from weak hash checks.
-
Unveiling Hidden Threats to Corporate Identities
- November 4, 2024
- Posted by: claudia
- Categories:

In today’s browser-centric workplaces, corporate identities serve as crucial defenses against data breaches. The “Enterprise Identity Threat Report 2024” reveals that 2% of users are responsible for most identity risks, often using weak credentials. This highlights the urgent need for improved identity security strategies.
-
LottieFiles Issues Warning About Compromised “lottie-player” npm Package
- November 4, 2024
- Posted by: claudia
- Categories:

LottieFiles reported a supply chain attack on its npm package “lottie-player,” resulting in the release of malicious versions that prompted users to connect cryptocurrency wallets. The compromised versions (2.0.5, 2.0.6, 2.0.7) have been removed, urging users to update to 2.0.8.
-
New LightSpy Spyware Version Targets iPhones with Increased Surveillance Tactics
- November 4, 2024
- Posted by: claudia
- Categories:

Cybersecurity researchers have uncovered a new version of iOS spyware, LightSpy, which enhances its functionality with destructive capabilities, capable of preventing devices from booting. The malware leverages known vulnerabilities through sophisticated attack chains, including varied plugins.
-
New Phishing Kit Xiū gǒu Targets Users Across Five Countries With 2,000 Fake Sites
- November 4, 2024
- Posted by: claudia
- Categories:
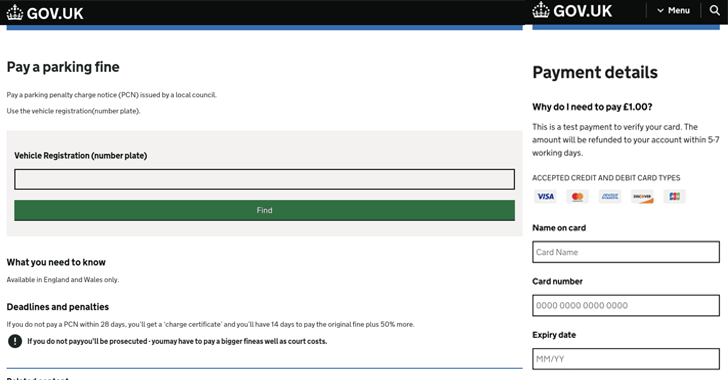
Cybersecurity experts have revealed the Xiū gǒu phishing kit, active since September 2024, targeting regions including Australia and the U.S. With over 2,000 phishing sites identified, it exploits Cloudflare for stealth and poses risks by simplifying attacks for less skilled hackers.
Contact us at the Consulting WP office nearest to you or submit a business inquiry online.
