Analysis of two arbitrary code execution vulnerabilities affecting WPS Office
- November 4, 2024
- Posted by: claudia
- Categories:
ESET researchers identified a code execution vulnerability (CVE-2024-7262) in WPS Office for Windows, exploited by a South Korean cyberespionage group known as APT-C-60, which was targeting East Asian nations. Their investigation revealed a method of exploiting the faulty code, leading to a second vulnerability (CVE-2024-7263). Both vulnerabilities have since been patched, and the blog provides in-depth technical details of these threats.
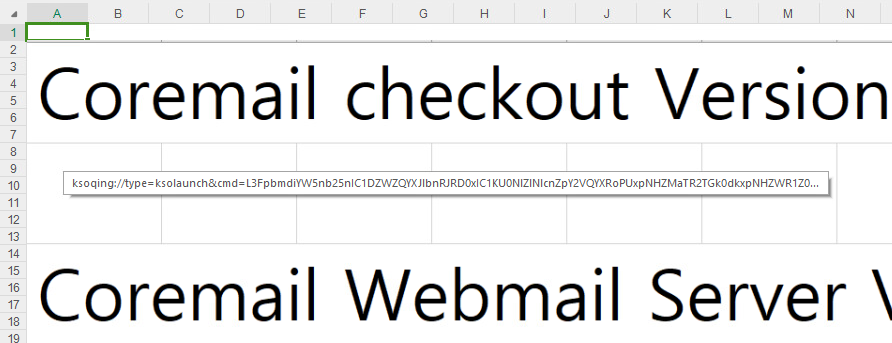
The first vulnerability (CVE-2024-7262) enabled APT-C-60 to craft malicious documents that would trigger an exploit when opened in WPS Office. The researchers discovered that the group had weaponized a spreadsheet document using a specially designed hyperlink, embedded within an MHTML export, which would execute an arbitrary library upon interaction. This exploit allowed for remote code execution, effectively functioning as a custom backdoor named SpyGlace, also referred to as TaskControler.dll by other researchers.
WPS Office has a substantial user base, with over 500 million active users globally, making it a significant target for cyberattacks, especially for espionage operations focused on East Asian countries. During the disclosure process, independent research by DBAPPSecurity corroborated ESET’s findings, confirming the exploitation of the vulnerability to deliver malware to users in China.
The vulnerability’s exploitation involved the use of a decoy image mimicking a spreadsheet’s interface, hiding the malicious hyperlink. Upon clicking a cell, the document triggered a series of commands leading to the execution of the attacker’s DLL. The timeline of the vulnerability’s discovery is outlined, detailing interactions with Kingsoft (the software’s developer) regarding patching the vulnerabilities and attempts to communicate the risks to users.
Analysis of the root cause indicated a failure in the sanitization and validation of paths being accessed, which allowed the exploitation of control flow to initiate code execution via WPS Office’s plugin component. The investigators explained the mechanics of the exploit in detail, including how MHTML files facilitated the download of remote libraries in a way that could be triggered by a mere click in the document or via Windows Explorer’s preview pane.
CVE-2024-7263 was discovered during the analysis of the patch for CVE-2024-7262. The patch introduced new checks but also revealed lapses in addressing security flaws properly, particularly concerning how variables were verified. This oversight could allow an attacker to leverage a modified path to load an arbitrary library, further underscoring the importance of rigorous patch verification processes.
The practical demonstration of the exploit presented how attackers could leverage a crafted environment to execute malicious actions using simple modifications to the paths provided in command line arguments. The ability to host malicious libraries in a local network also presents a significant security risk for unpatched systems.
Affected versions of WPS Office span from August 2023 until the patch’s release in March 2024, exposing users to vulnerabilities for an extended period. ESET strongly recommends that users update their WPS Office installations to mitigate these risks and protect against such sophisticated cyber threats.
In conclusion, the exploitation of these vulnerabilities highlights the ongoing threats posed by advanced persistent threats in specific geographical regions and emphasizes the necessity for developers to ensure stringent security measures and timely updates. ESET’s thorough investigation serves not only as a warning to users but also as a broader reminder of the complexity and dangers associated with software vulnerabilities in widely-used applications. Users are encouraged to stay informed and vigilant in their software management practices.
