New FakeCall Malware Variant Hijacks Android Devices for Fraudulent Banking Calls
- November 4, 2024
- Posted by: claudia
- Categories:
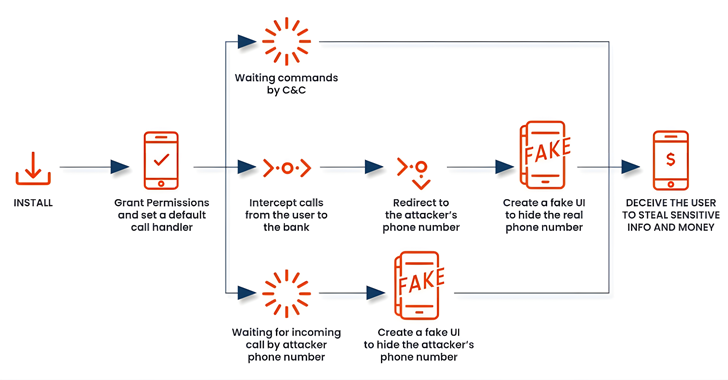
Researchers have identified an advanced version of Android malware known as FakeCall, which utilizes voice phishing techniques to manipulate users into revealing personal information. This malware, described by Zimperium researcher Fernando Ortega, takes significant control of mobile devices, intercepting calls and directing victims to dial fraudulent numbers controlled by attackers, all while masquerading as a legitimate user experience. The malware has existed since April 2022, predominantly targeting mobile users in South Korea, and has been closely examined by various cybersecurity firms, including Kaspersky and Check Point.
FakeCall operates under several package names that serve as dropper apps, such as com.qaz123789.serviceone and com.sbbqcfnvd.skgkkvba, among others. Similar to other banking malware that exploits accessibility service APIs, it captures on-screen information and gains necessary permissions to execute its malicious activities. The malware is equipped with a robust set of espionage capabilities, including the ability to access SMS messages, contact lists, GPS location data, and multimedia functionalities, such as taking pictures and recording video streams.
What sets this iteration of FakeCall apart is its method of coercing users to set it as their default dialer, thereby allowing the malware to monitor and manipulate all incoming and outgoing calls. The malware can alter dialed numbers, rerouting calls made to legitimate banking institutions to fraudulent lines, thereby deceiving victims into divulging sensitive information. This manipulation is further enhanced by the malware’s ability to simulate the actual Android call interface, convincing users that they are interacting with their real bank.
In previous versions, FakeCall prompted users to initiate calls to their banks through the app, pretending to offer loans at enticingly low interest rates. However, the recent advancements in the malware’s tactics illustrate its adaptability in response to enhanced security measures and caller ID technologies that help users identify suspicious calls.
To combat these threats, Google has begun implementing initiatives to block the sideloading of potentially harmful Android applications, especially those asking for accessibility permissions, in specific countries such as Singapore, Thailand, Brazil, and India. This development underscores the evolving nature of mobile security threats and the corresponding defensive strategies being employed to mitigate their impact.
The rise of sophisticated phishing strategies in the mobile landscape signifies not only a challenge for cybersecurity but also highlights the necessity for continued vigilance in protecting personal and financial information. Awareness and proactive measures against such threats remain critical in safeguarding against the deceptive tactics employed by malware like FakeCall.
