New FakeCall Malware Variant Hijacks Android Devices for Fraudulent Banking Calls
- November 4, 2024
- Posted by: claudia
- Categories:
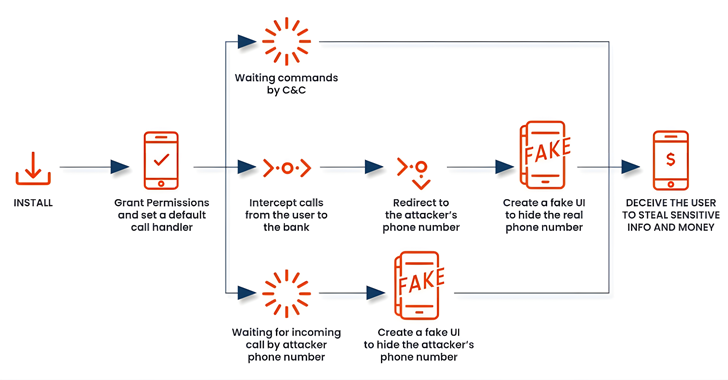
Cybersecurity researchers have identified a new variant of the Android malware family known as FakeCall, which utilizes voice phishing (vishing) techniques to deceive users into revealing personal information. This sophisticated malware takes extensive control of infected devices, including the ability to intercept both incoming and outgoing calls. Fernando Ortega, a researcher at Zimperium, outlined that FakeCall tricks victims into dialing fraudulent numbers controlled by attackers while mimicking a typical user experience.
Since its initial emergence in April 2022, FakeCall has been analyzed by several cybersecurity firms, including Kaspersky, Check Point, and ThreatFabric, and has primarily targeted mobile users in South Korea. The malware operates through various malicious package names (dropper apps) such as “com.qaz123789.serviceone” and “com.securegroup.assistant,” among others. It exploits Android’s accessibility services APIs to gain control of devices, capture displayed information, and acquire necessary permissions for further malicious actions.
Notable espionage features of FakeCall include the ability to capture SMS messages, contact lists, geographic locations, and installed applications. The malware can also access photos and record live video streams from both the back and front cameras. Additionally, it can manage contacts and audio recordings, and even simulate a video stream of user actions on the device through the MediaProjection API. The new variants also monitor Bluetooth status and screen states, significantly enhancing their capability to spy on users.
One of the most concerning functionalities enables FakeCall to prompt users to set the malicious app as the default dialer. This grants the malware oversight over all incoming and outgoing calls, allowing it to manipulate dialed numbers, especially those related to banks, redirecting them to rogue numbers controlled by attackers. Through these tactics, FakeCall can lead victims into actions they unwittingly undertake, endangering their financial security.
Previously, the malware variants enticed users to call banks from within the malicious app, falsely presenting as various financial institutions offering enticing loans. Ortega elaborated that when users attempt to reach their financial institutions, the malware redirects them to the attacker’s controlled number. The carrier of the malware presents a convincing counterfeit user interface that imitates the legitimate Android call interface, displaying the actual bank’s number, thus obscuring the fraudulent nature of the call from the user.
The rise of sophisticated mobile phishing strategies illustrates a worrying response from attackers to enhanced security measures and the widespread use of caller ID applications designed to flag suspicious numbers. In light of these evolving threats, Google has initiated measures to improve device security. This includes experimenting with a project to automatically block the installation of potentially unsafe Android apps, particularly those that request accessibility services, in regions such as Singapore, Thailand, Brazil, and India.
Overall, the emergence of the FakeCall malware variant reflects a significant escalation in the tactics employed by cybercriminals and poses an increased risk to individuals’ mobile security and financial safety. As such threats become more advanced, ongoing vigilance and security adaptations remain crucial for protecting users against malicious attacks.
