New Phishing Kit Xiū gǒu Targets Users Across Five Countries With 2,000 Fake Sites
- November 4, 2024
- Posted by: claudia
- Categories:
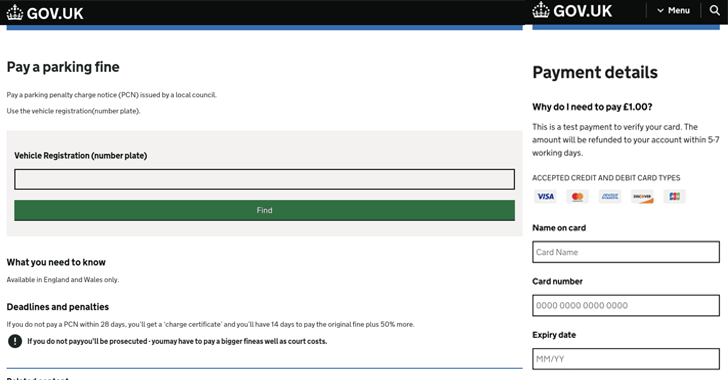
Cybersecurity researchers have unveiled a sophisticated phishing kit named Xiū gǒu that has been actively deployed in phishing campaigns against targets in Australia, Japan, Spain, the U.K., and the U.S. since September 2024. According to a report by Netcraft, this kit has facilitated the creation of over 2,000 phishing websites and has been utilized in attacks across various sectors, including public services, postal services, digital services, and banking. The use of Xiū gǒu is particularly concerning as it lowers the entry barrier for less experienced hackers, potentially leading to an increase in malicious activities and the risk of sensitive information theft.
Developed by a Chinese-speaking threat actor, Xiū gǒu features an admin panel and employs technologies like Golang and Vue.js for its operation. A distinguishing capability of this kit is its design to exfiltrate sensitive credentials from fraudulent phishing pages, particularly those hosted on the “.top” top-level domain, using Telegram as the medium for data transmission. The phishing attacks associated with this kit are disseminated primarily through Rich Communication Services (RCS) messages instead of traditional SMS, exploiting social engineering tactics that lure victims into clicking links related to fictional parking fines or package delivery issues.
The nature of these phishing scams is to manipulate victims into providing personal details and making illegitimate payments. RCS, an enhanced messaging system available on platforms like Apple Messages and Google Messages, supports file-sharing and includes features such as typing indicators. These messages commonly lead recipients to a shortened link, where they are phished for sensitive information under the guise of legitimate services.
In response to the rising phishing threats, Google has recently taken measures to enhance protections against such scams. The company has implemented improved scam detection technologies, leveraging on-device machine learning to filter out fraudulent messages particularly linked to job opportunities and package deliveries. Additionally, Google is piloting security warnings for text messages from unknown senders in select Asian countries, with plans to introduce these measures globally in the near future. This includes allowing users to automatically filter out messages from international senders not in their contacts by diverting them to a spam folder.
The security landscape also shows ongoing phishing threats targeting specific user groups, such as Facebook business account users in Taiwan. Cisco Talos reported a campaign aimed at these users, using deceitful emails that lead to the download of stealer malware disguised as a PDF file. Shark-jumping lures demand urgent compliance regarding copyright infringement, contributing to the malicious nature of the campaign which has been operational since July 2024.
Moreover, additional phishing campaigns leveraging popular brands like OpenAI have been noted, wherein businesses receive emails urging them to update payment information through obfuscated links. These campaigns reportedly trick recipients by employing tactics that allow them to pass basic email authentication checks, which can foster a false sense of security among potential victims.
The increasing sophistication of these phishing campaigns and the evolving tactics employed by cybercriminals underscore the critical need for heightened vigilance and improved protective measures against such security threats. As phishing schemes continue to adapt and proliferate, both individuals and organizations must remain aware and prepared to combat these evolving challenges to cybersecurity.
