Opera Browser Fixes Big Security Hole That Could Have Exposed Your Information
- November 4, 2024
- Posted by: claudia
- Categories:
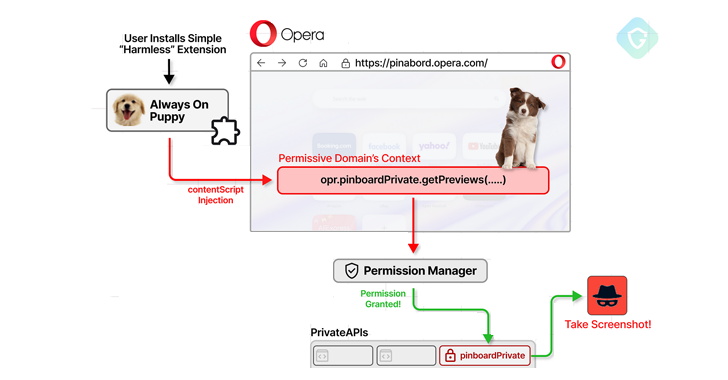
A recently patched security vulnerability in the Opera web browser, codenamed CrossBarking, raised significant concerns regarding the potential for malicious extensions to gain unauthorized access to private APIs. This flaw could enable attackers to perform a range of harmful actions, including taking screenshots, altering browser settings, and hijacking user accounts. Guardio Labs, which discovered the vulnerability, demonstrated the exploit by publishing a benign-looking extension in the Chrome Web Store designed to exploit the flaw once installed on Opera, marking an example of a cross-browser-store attack.
Guardio Labs emphasized that this incident underscores the ongoing tension between productivity and security, highlighting the sophisticated methods employed by contemporary threat actors who operate under the radar. Following responsible disclosure protocols, Opera addressed the security issues by September 24, 2024. However, this incident is not the first security risk associated with the browser; a previous flaw identified, known as MyFlaw, exploited a legitimate feature to execute files on the operating system.
The critical issue arises from several Opera-owned subdomains that have privileged access to the browser’s private APIs. These subdomains serve functionalities related to features like Opera Wallet and Pinboard, along with others employed in internal development. In particular, certain third-party domains also remain vulnerable, which further complicates the security landscape.
Guardio’s research revealed that while the browser employs sandboxing to isolate its context from the operating system, content scripts within browser extensions could inject malicious JavaScript into these overly permissive domains. This ability allows attackers to manipulate the Document Object Model (DOM), potentially leading to severe security breaches. An attacker with such access could capture screenshots of all active tabs, hijack accounts by extracting session cookies, and modify critical browser settings like DNS-over-HTTPS configurations.
These actions could facilitate advanced attacks, including adversary-in-the-middle (AitM) scenarios where victims are redirected to fraudulent sites masquerading as legitimate banking or social media platforms. To initiate such an attack, a malicious extension could be presented as innocuous and published in any legitimate browser add-on catalog, including the Google Chrome Web Store, provided it secures permission to execute JavaScript on relevant web pages.
Given the increasing number of rogue and deceptive extensions infiltrating official stores, this situation highlights the need for users to exercise caution when dealing with browser extensions. Guardio’s head, Nati Tal, stressed the significant influence these extensions can wield and called for stricter regulatory oversight. He recommended enhancing the browser extension review process by incorporating more rigorous continuous monitoring and requiring verified developer identities to prevent misuse.
In an official response, Opera acknowledged the vulnerability as part of their collaborative security efforts with third-party researchers. The company pointed out that while the identified vulnerability poses risks, it primarily exists in scenarios where users are misled into installing malicious extensions from beyond Opera’s Add-ons Store. Opera’s strict manual review process for its extensions is designed to mitigate risks of such infiltrations.
Moreover, the company emphasized a lack of evidence suggesting that this vulnerability was exploited in real-world situations, assuring that no Opera users have fallen victim to such exploits. Opera thanked Guardio for their collaborative approach and reiterated the importance of responsible disclosure within the software security framework, emphasizing its role in maintaining user safety.
Overall, the incident serves as a potent reminder of the cybersecurity challenges faced by widely-used web browsers and highlights the necessity for ongoing vigilance, improved regulatory measures, and user awareness in the realm of browser extensions.
